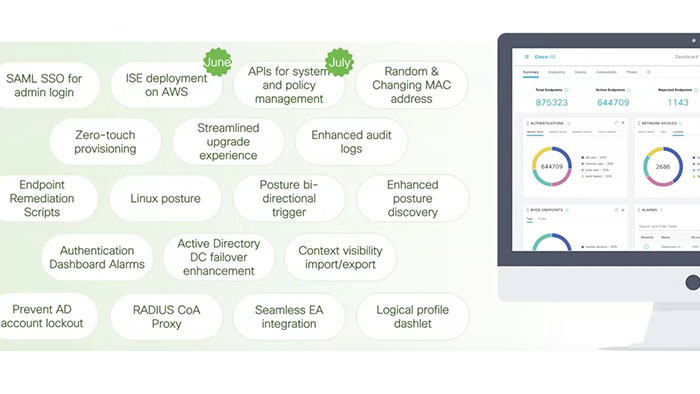
In this article we going to cover Cisco ISE 3.1 features and capabilities. ISE 3.1 release will support various new features such as deployment in AWS and tons of new API support for operations such as upgrades repository, certificate management and policies which applies to both Radius for the network access end users and TACACS plus for the device administration policies.
Moreover, ability to do posture on Linux clients, which will support Red hat SUSE and Ubuntu Linux is now available. Cisco is also introducing something called custom remediation script what it means is that you can push down a custom script as part of remediation for posture assessment on your Linux, Windows and Mac OS.
So previously, when you were doing remediation, meaning that you have an endpoint that connects and it does not meet the requirements, you had a certain set of things that you can do on the endpoint such as install a software, update the anti-virus or install the latest updates.
Now with Linux sponsor, Cisco ISE supports Red hat, Ubuntu and SUSE Linux and with the immediate custom remediation script you can craft a script that runs on locally on the computer. You can run it as the user, that’s been logged in, or the admin user that installed the AnyConnect client for that machine.
Also by introducing Device Unique ID, you can track the endpoints for devices that you own. It is integrated with the MDM as well as the BYOD flow within ISE.
Other exciting feature includes the admin single sign-on. So previously when you logged into the ISE admin GUI, you could only log in using the local accounts, AD accounts and Radius accounts. However, with the new enhancement that means that you can use single sign-on to log into the admin GUI using azure IDP or even Okta.
Cisco License is also enhancing the upgrade, so the time to upgrade has been reduced to like one third of time it used to be. Furthermore, by introducing some enhanced logging, you can see what is going on in terms of the changes that is been made to the system.
Finally, now you can bring up ISE nodes using zero touch provisioning whether it’s a SNS appliance or VMware or Amazon AWS. Now combine the zero touch provisioning with the API for management, you can bring any number of ISE nodes up and running and you can even create the policies for your deployment.
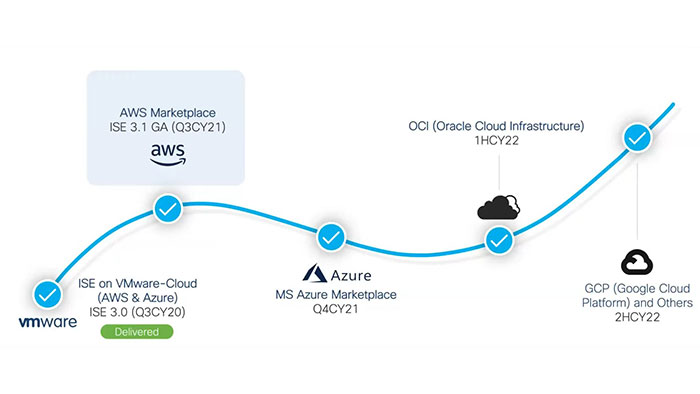
The 3.0 release, the ability to deploy ISE on top of VMware-cloud (AWS & Azure). Now, Cisco ISE 3.1 is available for AWS cloud and you can install it directly on Amazon AWS. Later this year, Cisco has the plan to expand support for Azure cloud and other public cloud vendors such as oracle cloud and google cloud.
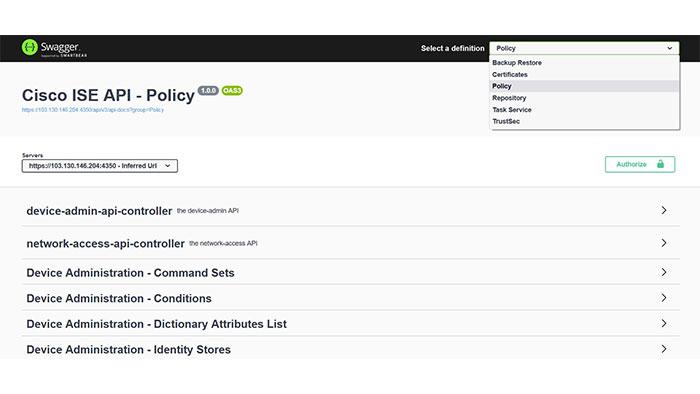
Basically, the idea of using APIs is to create, read, update and delete operations through https on different resources to control the configuration and operation of ISE. Cisco has been using ERS, MNT and pxGride APIs for years and now Open APIs has been added in Cisco ISE 3.1 to add some configuration.
The reason that Open APIs are interesting is because it’s a way that a lot of different companies are finally coming together with a common format or a standardized way of describing their APIs.
Cisco ISE 3.1

So the Linux is only supported with the full AnyConnect posture module. So you need to have the AnyConnect installed and the endpoint should be using properly signed certificate which means either a publicly signed ISE certificate or proper internal PKI that is deployed on the endpoints prior to deploying the AnyConnect posture module on the clients.
Distros that are supported are Redhat, SUSE and Ubuntu. Basically, there are two fundamental features of posture assessment. First, checking whether the client meets the requirement and the other one is the remediation, in case the device doesn’t meet the requirements.
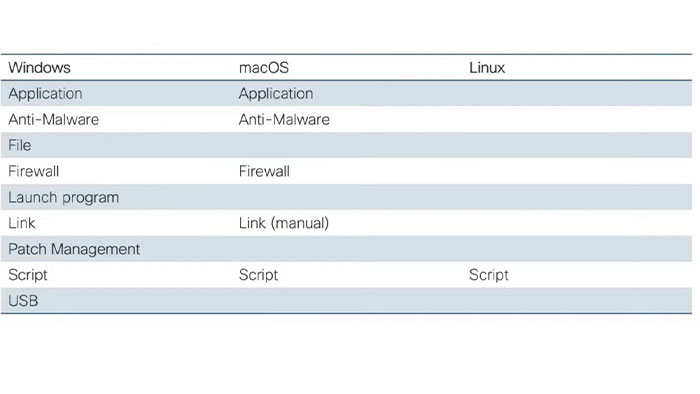
Some checks only work on windows and that does not work on Mac OS and Linux like for like registry check works on windows but it may not be supported on the Mac OS or Linux. Generally, it depends on the agent type that is used on the client. So, if you have the AnyConnect posture module which is called the full client, then you would have full capability of the posture assessment.
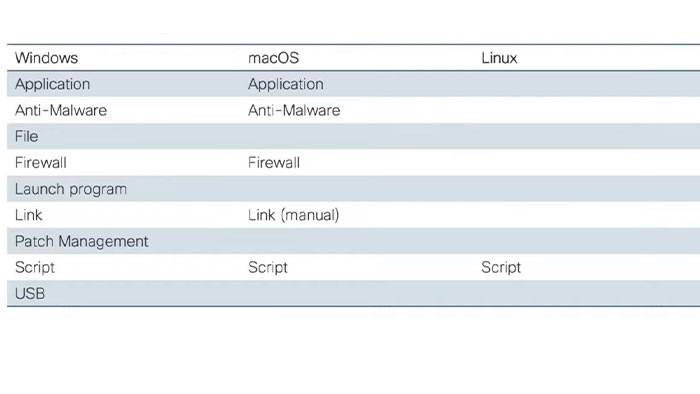
Whereas, if you use temporal agent which runs within a web browser or if you use agentless, then you’ll have some limitations on what you can do in terms of checks and remediation. You find posture checks is supported on different OS types in the following figure:
Cisco ISE 3.1
When it comes to the remediation, only option that we have available for the Linux is the script remediation.
Cisco ISE 3.1
Right now while Cisco team strives to be up-to-date, it is not always on point. Also there may be some custom applications that Cisco will never support. As a security admin there’s a need to mediate issues that causes the end point to be a non-compliant and move the endpoints to the compliance state.
So that they can be on the network and do their job. In an organization with thousands of endpoints or users, this needs to be done automatically without an admin being involved. So, admin needs to have a flexibility and this is where the custom remediation script comes into play.
This script option helps you to add some flexibility so that you don’t need to wait for any unsupported remediations. Plus, if there’s a new version of some software that you want to bring up, then you do not have to wait for the ISE to provide support for that application or anti-malware. You can create your script on your own and then take advantage of that.
Right now, on the windows power source script and on the Mac OS and Linux the shell script is supported and in this case it’s only supported on the full and connect agent. Therefore, if you have to use the any connect posture module, it is not supported on the client list nor the temporal agent.
When AnyConnect client connects to the network, if it sees that there is a network change or transition, it will start sending discovery packet to the default gateway, the discovery host and the enroll.cisco.com which is hard coded and all the PSNs that it aware of.
Now, Cisco ISE 3.1 have a new option where you can configure a list of PSNs that will be used for discovery. So, instead of all the PSNs that interconnect, you can designate one or two that you’ll be used for discovery.
In a very rare occasion, when you are using a like a non-VLAN based quarantine, where there’s an obvious change of IP address as you transition from the access VLAN to quarantine VLAN and back and forth, every time that happens AnyConnect will rescan the machine to make sure that the policy has been applied.
Now, when the AnyConnect comes up, even when it’s in access state, it’s going to keep probing the ISE to find out if that status is still true, and if that starts changes to pending meaning that is no longer compliant and then it will just go ahead, rescan the device and then make sure it’s compliant and get it back on the network.
Customers can upgrade ISE 3.1 by downloading ISE patches from software.cisco.com providing a few bug and vulnerability fixes such as Log4j vulnerability.