Cyber security is a multi-layered experience. While your business may be strong in one area, weaknesses in another can make it vulnerable to cyber attacks. While we’ve discussed the benefits of endpoint visibility through the Cisco Identity Services Engine (ISE), this type of segmentation is different from server-level micro-segmentation. The combination of Cisco ISE and server-level micro-segmentation provides the highest level of security to help prepare your business for attacks.
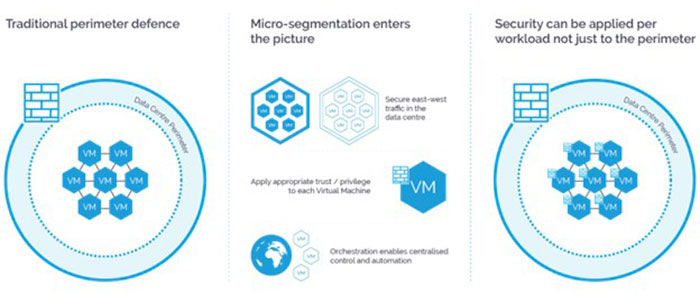
Micro Segmentation creates safe points in cloud environments and data centers to separate application workloads and secure them individually. By implementing MicroSegmentation, firewall policies limit traffic between workloads based on a zero-trust security approach, with the goal of reducing attack levels, preventing lateral movement of threats to contain intrusions, and increasing legal compliance. Micro Segmentation in a multi-cloud data center is also referred to as application segmentation or east-west segmentation.
Micro Segmentation provides a simple answer for protecting against exploits and threats, but here are some use cases:
When migrating to the cloud, users can now migrate workloads from on-premises data centers to cloud environments. However, it is important that your security posture is maintained after migration. These use cases will continue to grow as the need for a zero-trust security model becomes more critical.
Any business or businesses that processes credit cards is subject to strict legal and contractual compliance standards. This requires that all network traffic be segmented when payments are processed and remain independent of other network traffic. Today, Micro Segmentation can be used to support this requirement. That way, even if you are the victim of a cyberattack, the attack won’t move sideways and you won’t be able to access the cardholder’s personal data.
Micro-segmentation allows companies to answer the following questions:
This type of visibility allows companies to monitor suspicious activity in real time.

Without proper Micro Segmentation, an attacker who breaches the firewall can move sideways within the network. While a firewall keeps threats out, micro-segmentation focuses on understanding what is happening within the network and preventing the movement of threats.
Micro-segmentation ensures that users and devices can only access the parts of the network they need to do their jobs.
Every month, we see new security breaches that put sensitive data at risk. In all cases, it is becoming increasingly clear that malicious actors, regardless of industry or location, can not only gain access to sensitive assets, but also scale their locations undetected by workload. Unfortunately, companies that rely on outdated cybersecurity solutions that cannot keep up with the growing IT landscape are more vulnerable to these threats.
Micro Segmentation, a security method that divides a network into isolated segments that make it easier to monitor and manage traffic, is a huge advantage in protecting against advanced cyber threats. It can work well with Cisco Secure Firewall and Cisco Trust Sec. The advantage of micro-segmentation is that it provides security at a granular level, while also having the benefit of being defined as an abstraction rather than an IP address or VLAN membership. This provides increased security and simplicity as environment partitioning adapts to dynamic application environments.
Digital transformation has brought significant changes and new challenges to security teams. This is especially true when understanding remote access to networks and applications.
Micro Segmentation can help ensure access to applications by ensuring appropriate access processes for related functions or resources. The ability to provide visibility into all remote access points is especially important for companies that are spread across multiple geographies. A second-level micro-segmentation approach allows security teams to create flexible policy controls that are tailored to a user’s location, identity and role. This allows companies to secure micro-segment access to applications for both on-campus and remote users.
The right Micro Segmentation solution can be mapped into a single pane of glass, eliminating the need for multiple visualization and monitoring tools and providing a deep understanding of all data center resources and traffic between segments. Bare metal server and hybrid cloud environments require regular evaluation, which can sometimes mean significant recovery time. Centralized visibility into all segments of the data center helps reduce this time and keeps security strong.
Premium MicroSegmentation products allow you to create reusable security policy templates that address user access to applications and databases, as well as the relationships between workloads in different environments. This can save you a lot of time. Instead of spending hours on manual configuration tasks, companies can use templates to ensure consistent security and compatibility with any environment that is created or modified.
Data breaches can result from the unwanted or uncontrolled transfer of production data to a development environment. But historically, separating environments to limit access to sensitive data has been time-consuming and challenging, often requiring multiple stakeholders in distributed and hybrid data center environments.

An advantage of a micro-segmentation solution is that it allows for easy separation from the environment for modern data centers. Instead of using IP addresses and VLAN memberships, segment your network by marking resources hosting workloads or applications. As a result, environmental separation adapts to dynamic application environments, providing unprecedented convenience and operational safety.
With micro-segmentation, you get the benefits of reusable server role, environment and application tags, reusable security policy templates, cross-platform separation, automatic audit trail for each action, and a zero-trust network with complete visibility and control.
Threats come in a variety of forms, many of which are not easily apparent. These can weaken organizations that hold sensitive information and make them prime targets for data exfiltration. Advanced Persistent Threats (APTs) are orchestrated by a human or software moving laterally across the network and carefully planned to attack a specific entity.
Waiting time can be reduced by preventing malware from migrating beyond the initial attack surface to other nearby networks or resources. MicroSegmentation goes above and beyond by increasing security, making resources inaccessible to the threat. Interrupting any CNC communication will stop data exfiltration, resulting in timely containment and accelerated correction.