Cisco AnyConnect
Recently, by growing remote clients, Cisco AnyConnect VPNs have become more important. For millions around the world, working from home is a new norm for the foreseeable future causing organizations to quickly spin up and scale out VPNs to meet the high demand to the new remote workforce. With VPNs being one of the most obvious entry points inside our network, a poorly designed VPN rollout can have catastrophic implications.
2019 was a bad year for VPN vendors. Some of the biggest firewall and VPN vendors were played by vulnerabilities throughout the year. leading CISA to release several advisories of the vulnerable products and the impact to enterprises. In fact, the NSA and UK’s National Cyber Security Center reported that APT groups have been exploiting these disclosed vulnerabilities throughout the year.
As one of the technology leaders, Cisco AnyConnect counts as a reliable solution for clients to implement safe and reliable solution for site-to-site VPN and remote users access.
Due to the severity of these advisories, make sure your VPN appliance and endpoints software is not affected by any of the CVEs or CISA advisories. If it is, prioritize patching those systems as soon as possible that means both the VPN appliance and endpoints that they use to connect as well which both could have been affected depending on the vendor. Also, automated scanning BOTs can quickly sniff out and easily detect these vulnerable systems to be exploited later. In fact, that packet report showed a massive uptick in scanning for these vulnerabilities towards the end of 2019 and well into 2020.
VPN encryption technologies generally come in two different flavors IPSec or SSL and while both of these are considered generally safe the reality is that SSL and IPsec encompass a lot of different encryption algorithms, some of which are outdated and considered unsafe to use. For example, the term SSL is generally used interchangeably with TLS, but the actual SSL protocol is all vulnerable and should not be used under any circumstances.
In fact, all versions of SSL TLS 1.0 and TLS 1.1 should not be used for VPN deployment. That’s because they are susceptible to the poodle vulnerability and it’s not enough to simply not use these protocols they must be disabled or not supported altogether. because of the nature of the poodle attacks, they work by exploiting backwards compatibility to these older versions. While IPSec is less commonly used for endpoint connections here are some best practice advice when choosing configurations for your setup use version 2 whenever possible avoid weak encryption algorithms like DES or 3DES avoiding weak hashing algorithms like MD5 or SHA-1 and avoid Diffie-hellman groups 1 into.
One of the quickest and most effective measures you can take right now to harden your VPN is by enabling multi-factor authentication(MFA). Multi-factor means that users are required to enter their password and another form of verification such as something that possessed like a token or smartphone or something that they are like a fingerprint. For VPN multi-factor authentication, a common choice is to use a token based system where the user possesses either a key fob or an electronic Apple in their smartphone that displays the keys to enter once they’ve successfully entered their password.
Certificate based authentication serves as an additional form of verification for your VPN clients. Certificates provide verification for both the user and the corporation that users are connecting to. A user certificate can be revoked if an account becomes compromised while the device certificate can’t be revoked if a device is lost or stolen preventing someone who’s gotten their hands on the device from brute-forcing or trying to log in as a separate user name. While certificate to protect the corporation from unauthorized device connections into the network, they also protect the user from potential man-in-the-middle attacks. Without certificates, a simple DNS redirect his own attacker would need to redirect a client VPN connection to his/her own server without any form of verification from the client number.
As part of a good cybersecurity hygiene, we always tried to have segmentation wherever possible and this extends especially to remote users. That means, keep your VPN users in a separate IP space, using a separate way an IP from the rest of your corporate network and not allowing any intra-zone traffic. VPN users should be easily identifiable in network logs by having their own network IP space that also means users cannot communicate to each other unless they have it explicitly been allowed to. The idea here is that number one users always go through an exception device like a firewall. Also it allows you to apply a security inspection per firewall policy for example enabling DLP or antivirus for users talking to a network share.
Lastly you can also log in detect potential abuse from users in their network space using a SIEM. a good use case for this last point to do geolocation detection using a SIEM.
VPN connectivity has two fundamental methods Tunnel mode and split tunneling. In tunnel mode, once a user has connected to the VPN, all their traffic is routed through the VPN. However, in split mode only network you have specified will be routed through the tunnel and into your corporate network. The ladder sounds tempting because you lower the throughput requirements at your corporate edge however using split tunneling you’ve also bridged to network the untrusted internet from your client and your corporate network. Always be particularly cautious of any traffic that comes inside the network from the VPN.
Currently, using Cisco AnyConnect enable customers to benefit from all mentioned considerations. This solution can be integrated with Cisco Secure Firewall devices managed by Cisco FDM or Cisco FMC providing the needed infrastructure for remote clients and branches.
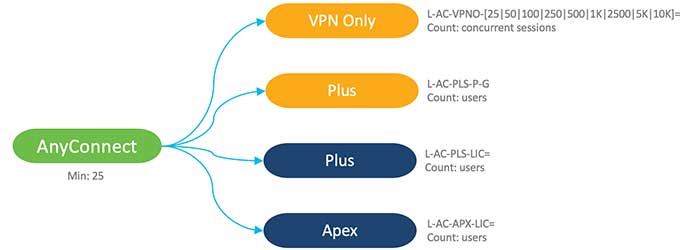
Cisco AnyConnect varies in different types which can be observed in the following figure: