
So, what is Cisco SD WAN? The Cisco SD-WAN SEN (Secure Extensible Network) is the story of applying software defined networking concepts to the wide area networking space while Legacy networking technology has become increasingly expensive and complex, and it cannot scale to meet the needs of today’s multisite enterprises. Legacy networking technology has become increasingly expensive and complex, and it cannot scale to meet the needs of today’s multisite enterprises.
What separates the Cisco SD WAN SEN from other SD-WANs is that it reimagines the WAN for a new generation of enterprise networks, separating the data plane from the control plane and virtualizing much of the routing that used to require dedicated hardware.
Basically, Cisco SD WAN is supposed to resolve the following WAN challenges:
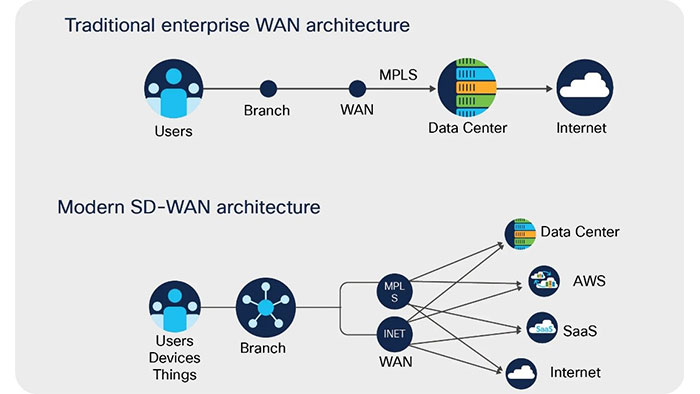
With traditional networking we saw the multiple transports being utilized but as the course of the years, transports are not just limited to the one or two. Enterprises are now seeing that there is any number of transports available in different geographic regions. That means, we may have MPLS, Metro Ethernet, LTE, Broadband, VSAT and etc. So, there is huge range of combination that customers can use to leverage the transport for their enterprises.
Cisco SD WAN SEN
What are the Cisco SD-WAN benefits? The core of the SD-WAN is SDN which stands for Software Defined Networking. SDN logically separates the control layer and the data layer within the underlying infrastructure abstracting control.
So the infrastructure can be automated and programmed from a common controller via software. Cisco SD WAN takes the principles of SDN and applies them to the wide area network. The WAN is the highway that interconnects enterprise resources to each other.
Now when we talk about the land we talk about transports or methods of connectivity some examples are broadband, Metro Ethernet, T1, MPLS and LTE. Usually we verbalize the LAN as a single entity but many organizations have more than one WAN, because connectivity will vary based on location and availability.
Each site could have combinations of MPLS, LTE or broadband and each transport is viewed as a separate WAN which is managed separately as unique addressing and may even have different providers. SD-WAN simplifies this and makes it easier to manage.
Plus, it takes all these different LANs and converts what used to be separate disparate networks into one common encrypted network managed by software. So why does SDN matter?
Achieve higher network performance and dramatically improve availability and application user experience by intelligently leveraging multiple paths. Gain visibility and active monitoring for the network and the applications running on it.
So the network becomes a single entity controlled from a single point increasing agility. You can quickly deploy new sites services or just more bandwidth with no truck rolls or on-site expertise. So Cisco SD WAN is a revolutionary technology.
it’s designed to streamline processes saving time and money, but more importantly turn a network into an application intelligent and fully automated software-defined infrastructure.
In this technology the WAN Edge device is uniquely identified by the chassis ID and certificate serial number. Hardware-based vEdge device certificate is stored in the on-board Tamper Proof Module (TPM) chip installed during manufacturing. Hardware-based Cisco IOS-XE SD-WAN device certificate is stored in the on-board SUDI chip installed during manufacturing. Finally, virtual platforms will be identified using a One-Time Password (OTP) provided by vManage to authenticate the device with the SD-WAN controllers.
Let us explore the components that makes Cisco SD WAN solution. This division of labor allows each networking layer to focus on what it does best. The control plane manages the rules for the routing traffic through the overlay network, and the data plane passes the actual data packets among the network devices. For this solution the following roles should be provided.
To deliver these capabilities the solution has four appliance types that will provide mentioned specific roles
Cisco vBond which is responsible for orchestration and initiates the bring up process of every vEdge device, at the first step it creates secure tunnel with vEdge and informs vSmart and vManage about its parameters like for instance IP address. It has to be fully connected with every device.
Cisco vManage that is a fully manageable centralized portal to run and operate software defined network (SD-WAN).
Cisco vSmart which is a controller for your network, it is responsible for managing all control and data policies by using special Overlay Management Protocol (OMP).
Cisco vEdge is a Viptella router which receive complete control and data policies from the vSmart, it is able to run routing protocol like OSPF, BGP to create connectivity on LAN side but also with MPLS provider if necessary. It establishes secure IPSec tunnels with others vEdges depending on selected topology.
Cisco cEdge is a IOS XE device running IOS XE SD WAN.
These four appliance types will make up the Cisco SD WAN solution. vBond, vManage and vSmart, are the virtual entities which can reside on premise or in the cloud. The most common consumption of this is as a service directly from Cisco. vEdge is an actual router that will leverage in this solution and could be in various form factors such as: ASR or ISR, Virtualized Routers like Cisco CSR1000v and Catalyst 8000 Edge Platforms.
You can find the terminology meaning of the terminology used to describe a Cisco SD WAN overlay network in the following:
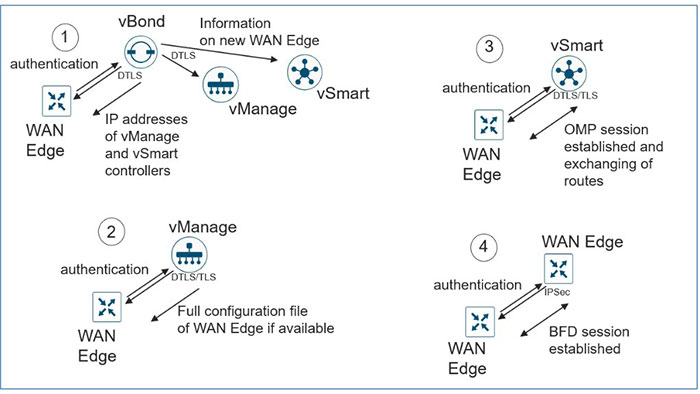
The SD-WAN controllers and vEdge/cEdge platforms need to mutually authenticate and trust each other before establishing the secure control connections. As soon as, the SD-WAN controllers authenticate each other and WAN Edge devices, they will validate the root of trust for the certificate root CA, compare the organization name and check the certificate serial number authority. You can find the SD WAN onboarding steps in the following figure:
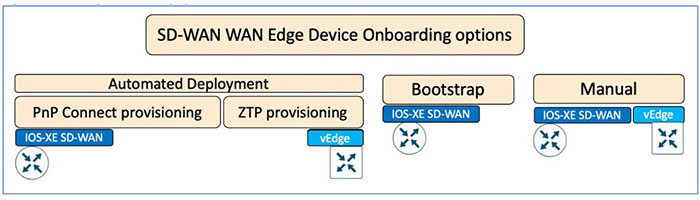
There are several options available to securely onboard SD WAN Edge devices. Generally, customers should use the PnP provisioning for their IOS-XE-based devices (cEdge) and ZTP for Viptela Edge (vEdge) devices. Also, Bootstrap config is only supported on the IOS-XE SD-WAN. All these features makes it easier to deploy new devices in the branch edges.
The cEdge device on boot up, obtains IP address, default gateway and DNS information via DHCP on the PnP interface that is connected to the WAN transport which is typically connected to the Internet. Then, the Cisco edge platforms try to reach PnP server at devicehelper.cisco.com and uses an HTTPS connection to get the required information about the vBond, including the organization-name.
After that, the vBond authenticates the device using its chassis/serial number and root certificate and provides the device with the vManage and vSmart controller information to the edge platform. Finally, the cEdge initiates and establishes secure connections with the vManage and vSmart controllers and downloads the configuration using NETCONF from vManage and joins the SD WAN overlay network.
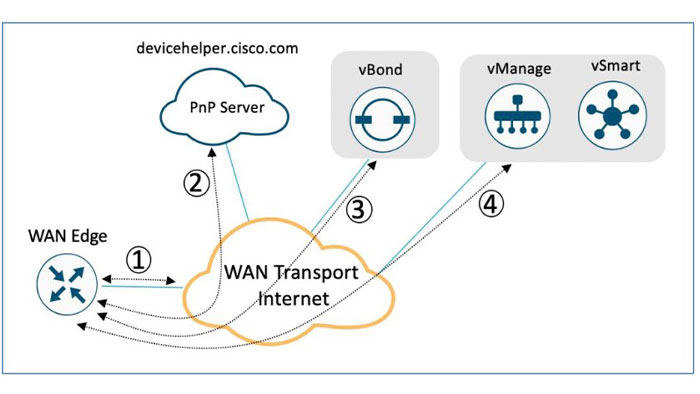
ZTP is as same as PnP provisioning process, though, it is for vEdge devices. In this process, vEdge devices try to connect to the ZTP server at ztp.viptela.com and uses an HTTPS connection to gather information about vBond orchestrator.
This option is available only for IOS-XE SD WAN WAN Edge platforms and not for vEdge devices. Leveraging bootstrap deployment requires the device template configuration to be built and attached to the WAN Edge device in vManage, after which the configuration file is built and shared with the WAN Edge device.
Plus, the template file should be placed on the device flash memory with the ciscosdwan.cfg name on the ASR1K, ISR1K and ISR4K and ciscosdwan_cloud_init.cfg on the ASR1002-X devices. Then, on the boot up, the cEdge device learns the vBond and organization name from the system template embedded in the configuration and initiates a secure control connection to the vBond orchestrator.
After successful authentication, the WAN Edge device receives information regarding the vManage and vSmart controllers and establishes secure connections with vManage and vSmart and downloads the entire configuration and joins the Cisco SD WAN overlay network.
For manual deployment, customers need to manually enter the whole configuration, such as System-IP, Site-ID, organization-name and vBond information and configure the transport VPN (VPN 0) interface with IP address, route and tunnel configuration.
As we want to deploy branches in a simple fashion across any transport to leverage anything and everything to bring up all of our sites as quickly as possible. Moreover, the way that applications are consumed are changing. So we want to be able to leverage the fact that our network should now also be able to extend into any types of endpoint such as: Private Cloud, Colocation and Public Cloud. So the transport that is used to connect our network allow us to connect to any type of infrastructure to deliver required quality of experience. Finally, no matter what transport we used, everything has to be encrypted and secured.
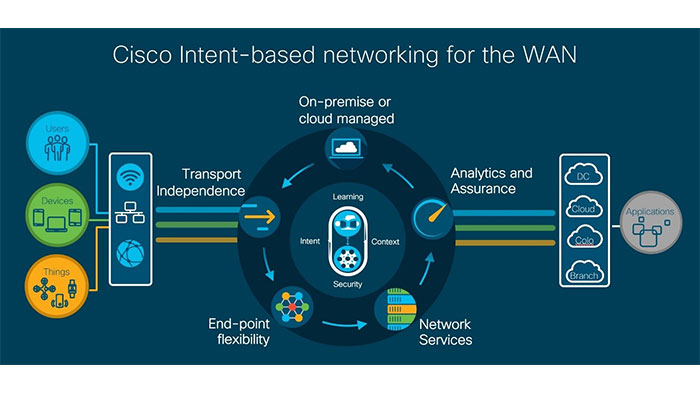
Cisco SD-WAN SEN
In the Cisco SD WAN framework, essentially, there are four main things to remember. The first thing is, Secure Transport Fabric. Plus, it provides Application visibility and QoE including what are application patterns look like and what are the quality of the experience for those applications and it allows you to tune what path needs to be taken and what QoE to have for your applications. The third thing is the means to consume these services. The ability to consume this in any shape of form such as, physical or virtual appliance, rich services or cloud-ready applications, is critical to your long-term planning. Finally, everything will be delivered through the cloud giving you rich analytics to see what is happening in your environment, what to do about it and how to change so your network experience gets better.
Intent-Based Networking boils down to three main aspects, Translation, which allows you to capture business objects, Activation, which enables the translate business goals into policy directives, and assurance which provides visibility into what is happening into your infrastructure. All these capabilities would be delivered by Cisco vManage.
The security features available in the security policy dashboard on Cisco vManage enable the following capabilities within remote sites running IOS-XE SD-WAN WAN edge platforms.
vManage includes predefined workflows to facilitate several use cases based on intent, such as:
In addition, you can build your own custom policy by combining a custom variety of security features. Security features such as Application Firewall and IPS enabled on your WAN edge devices, enables customers to restrict access to certain Internet destinations for remote employees and guests, protect the internal network from malware in real-time and eliminate further cost to deploy any additional security equipment. Finally, using central management, makes it more intuitive to troubleshoot and monitor the Cisco SD WAN overlay solution via the Cisco vManage GUI.
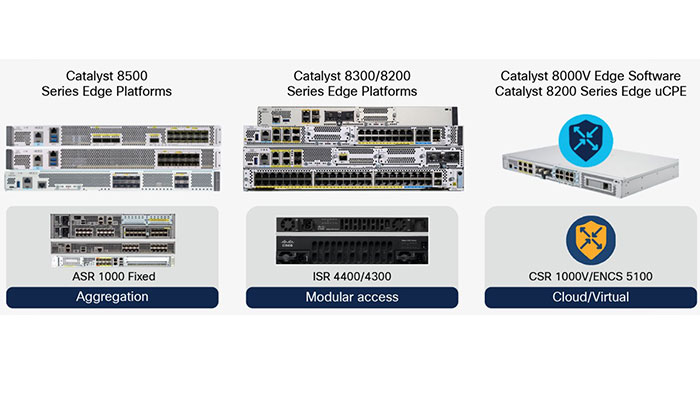
Lately, Cisco Catalyst 8000 edge platforms are announced as a new Cisco SD-WAN edge platform which can drive many new features and delivers SD WAN success. These new flexible edge platforms support SD WAN and cloud networking use cases and there are three major platforms within the Catalyst 8000 family:
The Cisco Catalyst 8500 is designed to replace the ASR 1001-HX / ASR 1002-HX and is positioned at the data center/colocation for extremely high performance.
The Cisco Catalyst 8300 is designed to replace the ISR4400 and is positioned at the branch. This innovative platform offers very good performance but also focuses on delivering services like switching, VoIP, security and more at the branch in a compact footprint.
The Cisco Catalyst 8000v is positioned to replace the CSR100v. This one is designed to run in virtual environments and on cloud marketplaces such as VMWare ESXi and Amazon AWS.
The Catalyst 8000 Is More Than a Router
So What the is an edge platform really? Well, these platforms can do a lot more than just routing. The Cisco 8000 series platform offers a lot of compute power which can be put to use to run KVM based containers such as Thousand Eyes, Wireshark and more. Also IOS-XE SD-WAN mode provides strong support for programmability and automation. These devices can be interacted with via custom automation and programmability solution, or through Cisco’s campus automation tool DNA Center, or the company’s WAN automation tool vManage.
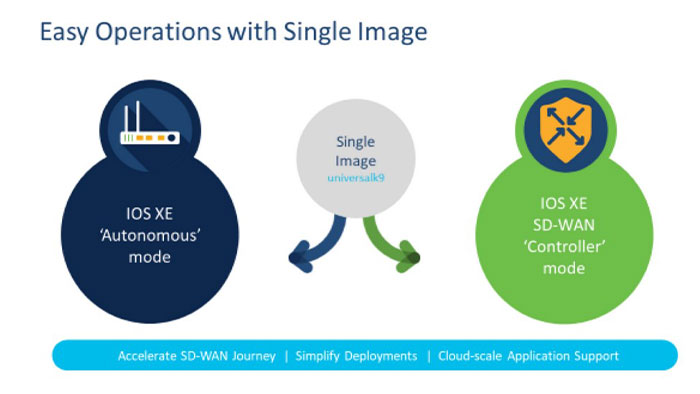
Previously, if you wanted to run the Cisco SD-WAN feature set, you had to install one image and If you wanted traditional IOS-XE, you had to install another image. However, after IOS XE 17.2, you can use a universal binary and boot into whichever mode you want. Be sure to back up your config when moving between images as there are some circumstances where it can get blown away.
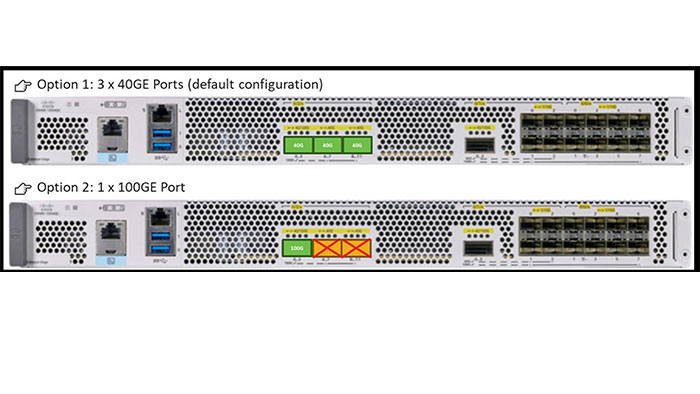
40G and 100G Interfaces
Nowadays, WAN and LAN interconnects are getting faster. Cisco Catalyst 8000 series can provide 40G and 100G connections which are required to deliver more powerful and consistent services. Powered by the all-new third-generation QuantumFlow Processor (QFP) Application Specific Integrated Circuit (ASIC), the Cisco Catalyst 8000 series platforms can enable this connectivity and forward high levels of IPSec throughput. If you’re still utilizing 10G/1G ports, these platforms can offer high-density port counts for those use cases.
Cisco DNA subscriptions for SD-WAN delivers advanced application policy and experience-based analytics and assurance. SD-WAN subscription offers are categorized into better and best solutions:
Also, crypto bandwidth entitlements for IPsec tunnels can be maintained using these subscriptions which can be applied either on Cisco vManage or Cisco DNAC.

Cisco DNA Essentials enbales the following features on devices:
Cisco DNA Advantage enables the following features on devices:
Cisco DNA Premier enables the following features on devices:
Cisco DNA Premier supports the following platforms: