
Cisco Secure Endpoint
Cisco Secure Endpoint (formerly AMP for Endpoints) integrates prevention, detection, threat hunting and response capabilities in a single solution, leveraging the power of cloud-based analytics. Secure Endpoint will protect your Windows, Mac, Linux, Android, and iOS devices through a public or private cloud deployment.
Cisco AMP for endpoints is a next-generation endpoint security solution that protects your organization from the most advanced cyber-attacks.
AMP for endpoints can prevent attacks and block malware at the point of entry but also if something manages to get inside it provides continuous monitoring and threat detection to quickly spot malicious behavior and response capabilities to quickly contain and eliminate threats of for damage.
It can be done to prevent attacks global threat intelligence from Cisco Talos group is used to strengthen network defense’s file signatures, fuzzy fingerprinting and other detection engines are used to block malware at point of entry.
Obviously, you can’t always prevent 100% of attacks. AMP continuously records and analyzes all file activity processes and communications on your endpoints to rapidly detect a compromised device.
This continuous recording and analysis provide security teams with a holistic view of activity across all their endpoints including PCs, Macs, Linux and mobile devices. AMP shows you the complete recorded history of events seen on the system this enables what we call retrospective security.
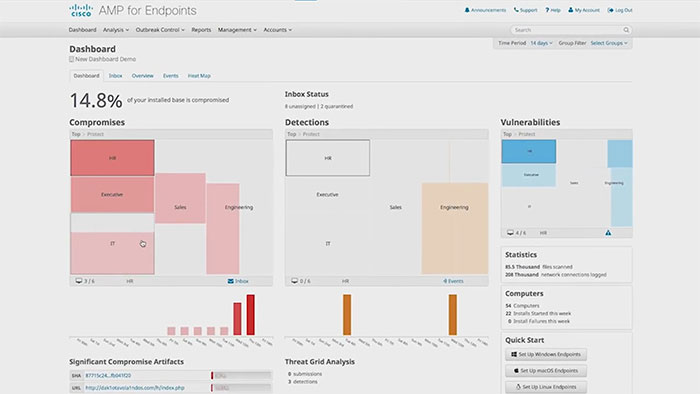
Cisco Secure Endpoint
It has the ability to rollback time on the attack to see everything that happened, giving you a level of deep visibility context and control to quickly detect attacks scope a compromised and remediate malware before it causes significant damage. When it comes to malware time is everything.
The industry’s average time-to-detection is 100 days though AMP can detect malware in hours or even minutes. From AMPs easy-to-use browser-based management console, you can protect your organization using these powerful capabilities indications of compromised devices help you identify attacks before they fully materialized.
AMP automatically correlates file events with malicious behavior events to uncover and prioritize coordinated attacks trajectory shows you the complete ancestry of a threat on a single device like the origin of the threat, what it’s doing, what applications that’s affected parent processes, connections to remote and unknown files that may have been downloaded by malware trajectory.
Then AMP lets you pivot your view from one endpoint to all endpoints to see all the machines that have encountered that threat. File analysis pulls information from built-in sandbox powered by threat read to show you even more detail like threat scores, behavioral indicators, screenshots of the malware, executing and sample packet captures.
Outbreak control lets you stop the spread of malware automatically or with just a few clicks. For instance, if you see malware on one endpoint and want to stop its execution on all endpoints on the network, simply right-click add it to a block list and the file will be quarantined and not allowed to execute on all endpoints full stop.
low prevalence shows you files across your endpoints that are kind of flying under the radar executed by only a few users and this lets you further analyze those files to see if their malicious. Vulnerable software feature shows you all the software on your endpoints that is currently vulnerable to malware so you can quickly patch them.
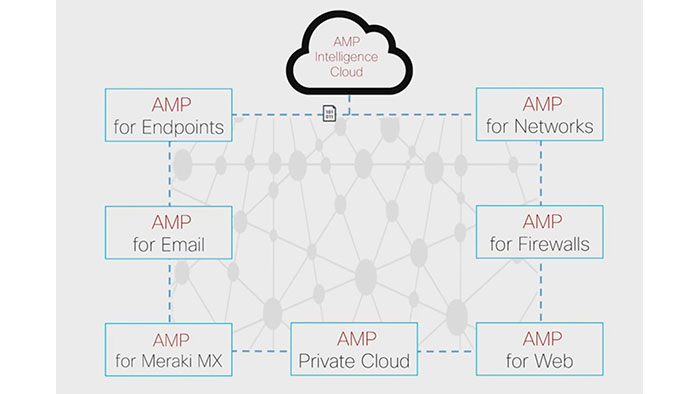
AMP can also automatically remediate systems without a full scan. The technology continuously cross-references files analyzed in the past against the latest threat intelligence and retro actively quarantined any files that were previously deemed clean or unknown that are now known to be a threat.
In fact, all this analysis is done in the cloud. gone are the days of a resource-hungry endpoint client that affects users and breaks a machine. With amp the cloud and endpoints communicate via amps lightweight connector with no noticeable performance impact on users.
And finally, AMP has an API that lets you sync it with other security tools or SIMS (Security Information Management Systems) but most importantly AMP for endpoints is part of the larger integrated security ecosystem that cisco has built to protect its customers. threaded information is shared and correlated amongst ant for endpoints and the network IPS, firewall web proxies, email gateways and more so that.
if you see a threat in one place you can be protected everywhere. Some of these capabilities let you make more informed security decisions accelerate investigations, simplify endpoint security management and drastically reduce the time-to-detect contain and remediate.
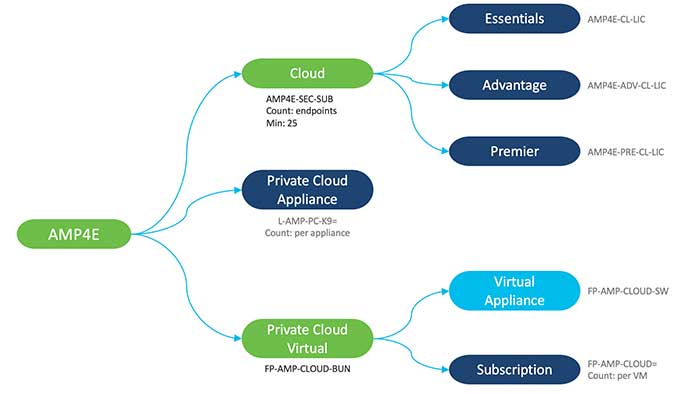
Cisco secure Endpoint smart license is available in following three tiers:
AMP for Endpoints Advantage License: Contains all above plus following features:
AMP for Endpoints Premier: Contains all above plus following features: