Cisco Secure Workload (Tetration)
One of the key data center challenges that many customers struggle with is to build a secure infrastructure for their application workloads. There is a high-level of complexity because modern applications are dynamic and distributed across on-prem and multi cloud environments. As a result, traditional parameter base security is not sufficient and a new approach is needed.
Cisco Secure Workload (Tetration) platform is designed to address this complex environment in a very comprehensive fashion. It dramatically simplifies the implementation of a zero trust model within the data center using whitelist policies. In addition, it enables multidimensional workload protection no matter what type of infrastructure the applications are in.
To help reduce the attack surface and prevent lateral movement from hackers, application segmentation allows you to automate policy models with fine-grained enforcement so segmentation and application whitelisting become more adaptive, attainable and effective. Cisco Tetration auto generates the granular whitelist policy for applications based on application dependency, its communication and behavior.
This behavior based analysis model allows you to keep the policy up to date depending on business requirements you can also integrate any predefined set of policies with this auto-generated whitelist. You are able to enforce these granular policies to enable consistent application segmentation irrespective of the infrastructure type, whether it is a bare metal virtualized or container environment, Whether the application is running in an on-prem data center, public or private cloud.
Implementing consistent segmentation allows you to control lateral movement across east-west traffic to minimize the damage from a security incident.
Next step is to baseline the behavior of the processes running on the servers, then apply models to identify any behavior deviations and compare them to known bad patterns exhibited by these processes. When these indicators of compromise are detected early on, you can minimize the impact by faster remediation. Last but not least keeping an accurate inventory of software packages and versions installed on the servers and then identifying common vulnerabilities and exposures associated with them is also key. This enables you to significantly reduce risk and threat exposure from known vulnerabilities.
Cisco Tetration using machine learning and behavior analysis lets you generate the application dependency map which acts as the blueprint for the whitelist policy recommendation. this map shows various components that are part of the application such as web, middleware, database and their communication and dependencies between them.
Cisco Titrations automated enforcement allows you to enforce this highly granular whitelist policy using operating system capabilities on the server itself. Cisco Tetration automatically normalizes the policy and enforces it on all the servers there are part of the application workspace. This allows you to realize a consistent segmentation for mission-critical applications running on bare metal servers, virtual machines and containers. This capability also provides an infrastructure agnostic approach to securing applications across on-prem data centers, public and private clouds.
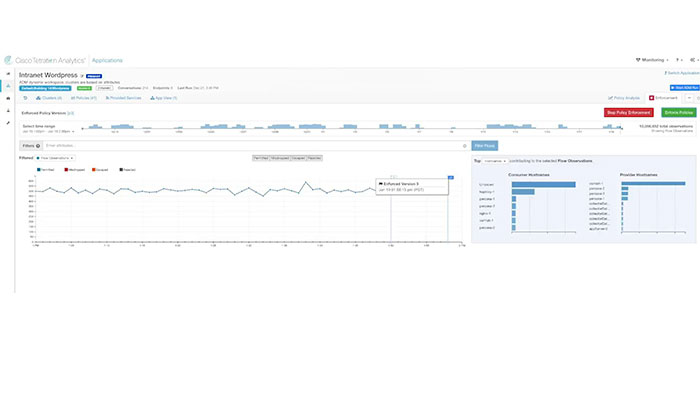
Today cisco Tetration supports policy enforcement capability on more than 50 operating systems. Cisco Tetration also monitors for compliance deviation on a minute-by-minute basis. When an application communication deviates from its policy an alert is generated which can be integrated with any security incident and event management system.
In addition to segmentation, Cisco Secure Workload collects and baselines the process details running on each of the servers. This information includes process ID, process parameters, user associated with that, process start time and process hash information. In Cisco Tetration we have reverse-engineered and modeled malware and its behavior patterns to identify process behavior deviations. Security operations can define rules for specific events and associated actions Windows occur using simple to express language.
Finally, Cisco Tetration platform also baselines the installed software packages, package version, patch level and etc. It verifies if any of these software packages have common vulnerabilities and exposures.
When a vulnerability is detected you can find complete details including the impact and the exposure scores. Security operations can also predefined policies with specific actions such as quarantining a host when servers have packages with certain vulnerabilities. This capability can be used to identify broad set of CVEs including high impact vulnerabilities such as spectre and meltdown.
To put it in the nutshell, Cisco Secure Workload (Tetration) can be implemented as a holistic workload protection strategy to achieve a common business goal.