By following this introduction, you will be able to configure the FDM (Firepower Device Management) On-Box management service and with Cisco FMC for Firepower Threat Defense series with FTD (Firepower Threat Defense) installed.
The following software and hardware versions should be implemented:
All devices are supposed to start with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Generally, you have two options to manage the FTD installed on a firepower:
Be aware of that you cannot use both the FDM and FMC to manage an FTD installed in a firepower 2100. Once the FDM On-Box management is enabled on the firepower 2100 FTD, it won’t be possible to use an FMC to manage the FTD, unless you disable the local management and re-configure the management to use an FMC. On the other hand, register the FTD to an FMC disables the FDM On-Box management service on the FTD.
Caution: Right now Cisco does not have any option to migrate FDM firepower configuration to an FMC and vice-versa, take this into consideration when you choose what type of management you configure for the FTD installed in the firepower 2100.
The management interface is divided into 2 logical interfaces, br1 (management0 on FPR2100/4100/ 9300 appliances) and diagnostic:
| Management | Diagnostic | ||
| Purpose | · This interface is used in order to assign the FTD IP that is used for FTD/FMC communication.
· Terminates the sftunnel between FMC/FTD. · Used as a source for rule-based syslogs. · Provides SSH and HTTPS access to the FTD box. |
|
|
| Mandatory | Yes, since it is used for FTD/FMC communication (the sftunnel terminates on it). | No, and it is not recommended to configure it. The recommendation is to use
A data interface instead (check the note below). |
|
The benefit of leaving the IP address off of the diagnostic interface is that you can place the management interface on the same network as any other data interface. If you configure the diagnostic interface, its IP address must be on the same network as the management IP address, and it counts as a regular interface that cannot be on the same network as any other data interfaces. Because the management interface requires internet access for updates, putting the management interface on the same network as an inside FTD interface means you can deploy the FTD with only a switch on the LAN and point the inside interface as the default gateway for the management interface (This just applies when the FTD is deployed in routed mode).
Note: You can use the FXOS GUI (Graphic User Interface) called FCM (Firepower Chassis Manager) or the FXOS CLI (Command Line Interface) to configure firepower chassis functions; However, the GUI FCM is not available when the FTD is installed on the firepower 2100 series, just the FXOS CLI.
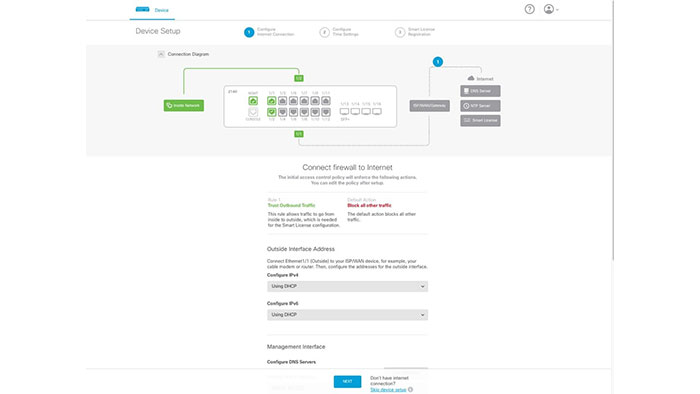
In order to enable the FDM On-Box management on the firepower 2100 series proceed as follows.
firepower# connect ftd
Note: Assign your management IP/Mask/Gateway based on network topology. 3. Configure the management type as local.
>configure manager local
>configure https-access-list 0.0.0.0/0
Caution: It is recommended to assign more specific IPs.
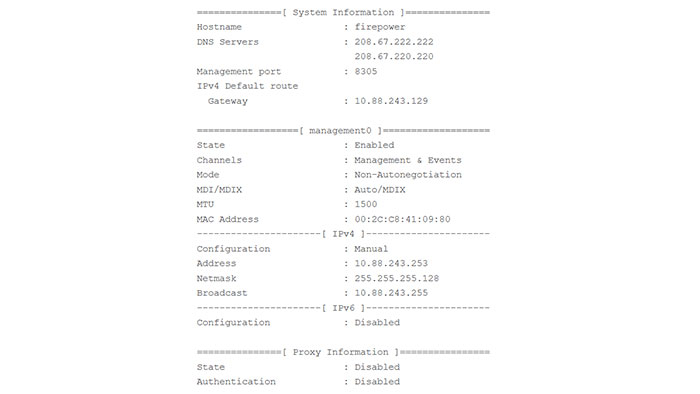
You can verify the network settings you configured for the FTD with the below command.
> sho network
By default, Cisco Firepower Threat Defense is managed locally with Firepower Device Manager.
>show managers
Managed Locally.
Locally is referring to FDM .
>configure manager add [FMC IP Management IP Address] [Registration Key]
Note: If you have any feature licenses enabled on the FDM you need to disable them first otherwise these licenses remain assigned to the device in Cisco Smart Software Manager.
It is changed to FMC though the registration is still pending and you need to move to FMC and input similar configuration with same registration key.
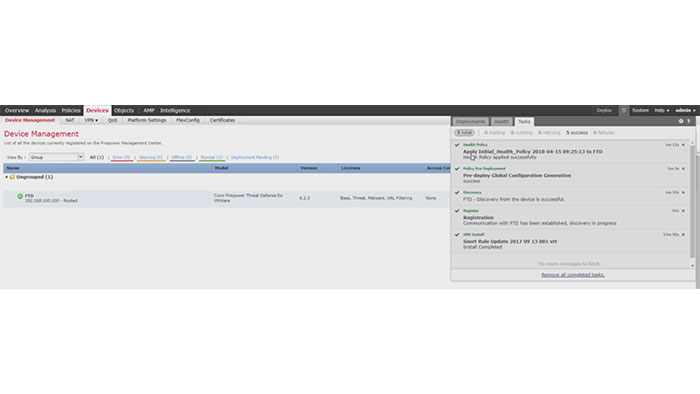
In the Host field Enter the FTD’s Management IP, for Display Name enter a custom name for the device and final, put your Registration Key in the third field.