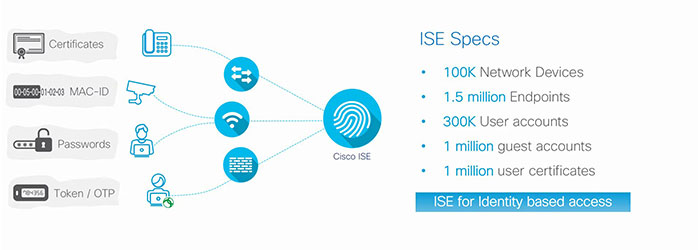
Cisco Identity Service Engine (ISE) is a network access control and policy enforcement platform. Network devices are the main avenues for wired network, Wireless and VPN connection to allow the users and the endpoint to connect to the network to access various services. With the help of credentials such as password, certificates, tokens or at least the endpoints MAC address. Now these credentials reach ISE in a process called authentication.
Also, there are various authentication protocols that an enterprise can use depending on the type of network and endpoint. So, essentially, with authentication you tell ISE who you are. In addition, authentication typically ends with an authorization. So once you revealed your identity to ISE, it determines the level of your level of access based on the generated a session ID that the endpoint sent to the ISE once it got connected. Cisco ISE centrally knows what are all the endpoints in the network and where they are located. So with all this in consideration, how does ISE fare in terms of identity based access?
ISE can talk up to hundred thousand network devices, can support up to 1.5 million endpoints, 300,000 internal user accounts, 1 million guest user accounts and 1 million user certificates that can be issued from ISE. That’s quite a lot what Cisco ISE can deliver however when you look at enterprises today, they do have some infrastructure running that already has some of these identity services like Microsoft Active Directory or an LDAP server.
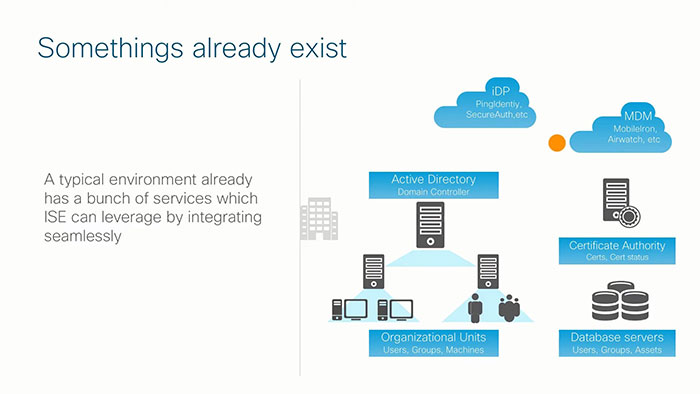
Basically, the endpoints want to connect to the network, the network devices gate the access, then Cisco ISE determines who should get what level of access by resolving the identity from the external identity sources. Once someone authenticates, ISE builds a session table listing all the users and their specific association to the network. Each endpoint that shows up in the network sends out some interesting traffic that reveal the endpoint type. For example, the DHCP class identifier as MSFT tells ISE that it’s a Microsoft workstation.
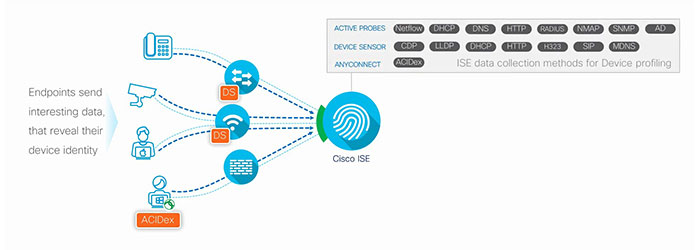
So either these traffic somehow hits directly to ISE, or you can use this tiny feature on the network devices called the device sensor(DS) that caches such interesting traffic and passes it on to the ISE over RADIUS. Once ISE receives the attributes, based on the profiling policy, it can classify the endpoint into specific device groups and with the help of a feed service you can keep the profiling policies up to date.
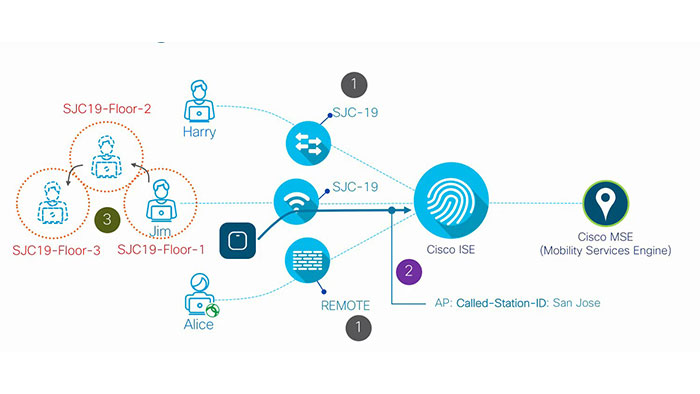
The end result is that you will see endpoint profile associate to the endpoints MAC address telling us what device it is. When you author time-based policies within ISE, you can in one simple way, determine the location which has a location label assigned to the network devices and then tracking where the authentication request is coming in from.
If it is coming in from a switch, that is labeled as a SJC-19 location, then you can apply specific policies. In a wireless network the access point’s call station ID can be defined with the location name. thereby, it is telling us which location the wireless user or device is. Lastly, if you integrate ISE with mobility services engine (MSE), then you can track the actual physical location of the wireless endpoint as it moves.
Wired, Wireless or a VPN device, has its specific RADIUS attributes that tells the details of how they’re connecting. For posture or compliance of the endpoint, you need Cisco AnyConnect agent on the endpoint. for this, basically you can have a posture policy on Cisco ISE, that tells AnyConnect to check on certain things to consider at the endpoint to be compliant.
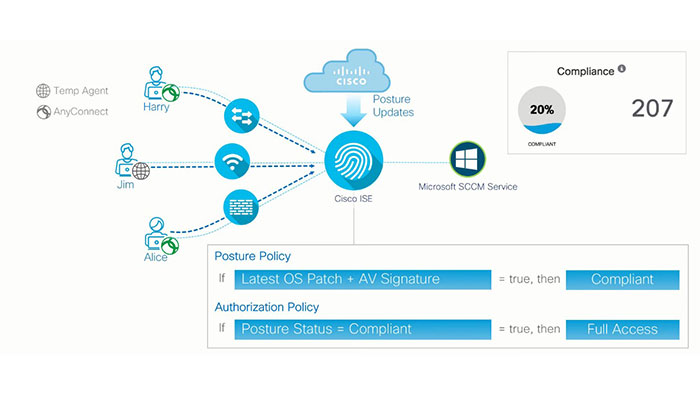
These checks could be OS patch level, antivirus signatures, presence of a USB storage and much more and then the automation policy can be defined to act on the posture reserved. If someone is compliant, then you can provide full access if not, you can provide access to the remediation services.
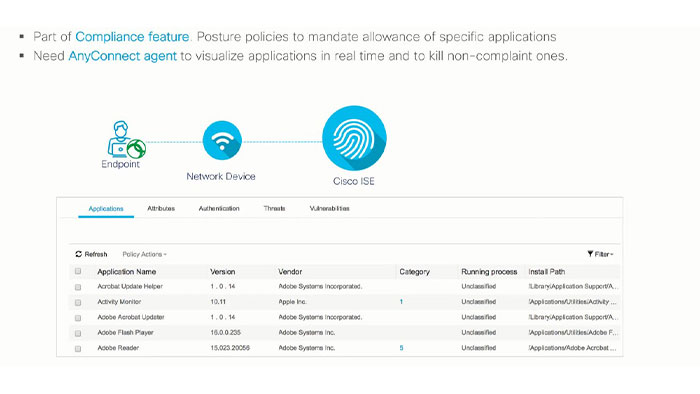
Compliance for mobile devices is done by integrating ISE with the mobile device management (MDM) solutions. You can check on a bunch of things like PIN lock, Jailbreak status of the mobile devices and much more. The partial functionality allows you to look and list all the applications installed and running on the endpoints. You can also initiate a kill or an uninstall function for specific applications right from the ISE dashboard.
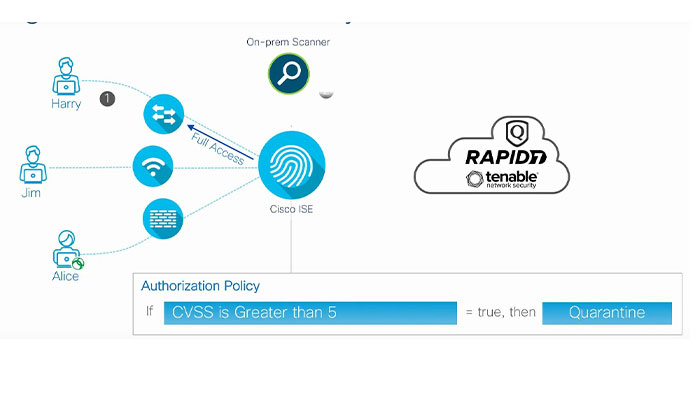
Cisco ISE can integrate with the vulnerability scanners such as Rapid7 and tenable security to control network access based on the CBSS core. Here, CBSS stands for common vulnerabilities coding system which is a number from one to ten that tells the one ability status of the endpoint. If the number is higher it means the endpoint is highly vulnerable. In terms of the flow, let’s say the endpoint connects and gets full access.
ISE can mark the endpoint for the word abilities can and as the on-prem scanner for a vulnerability assessment. The scanner scans the endpoint and reports the CBSS to its mothership. After that, ISE pulls the score and then applies the authorization policy. If the policy says that a CBSS is less than five, must be quarantined then ISE who will ask the network device to quarantine the access to the same point.
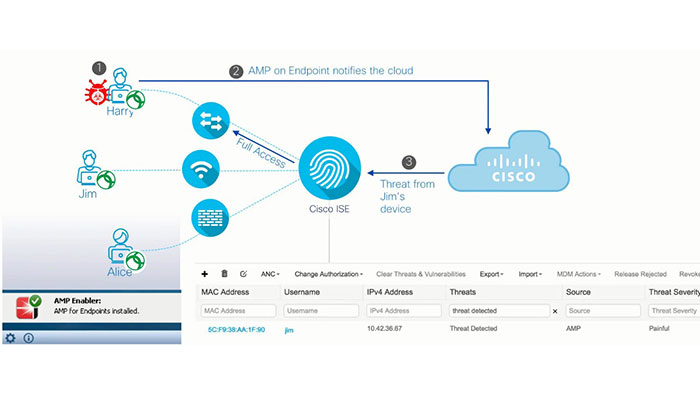
Lastly, Cisco ISE can build threat context when integrated with AMP or CDA. With AMP, when an endpoint that is installed with AMP, gets infected, it will report this incident to the AMP cloud and then the threat score will show up in ISE dashboard. The administrator can up to quarantine this uses device later.